A Cyber Security Company
We invite you to explore our resources, products, and services tailored to meet the needs of both beginners and seasoned professionals. From software and hardware solutions to cybersecurity and network management, we offer many options to help you achieve your goals.

Cyber Security Operations
Red Team
The Red Team in cybersecurity focuses on simulating real-world attacks by thinking and acting like hackers. Their goal is to find vulnerabilities, exploit weaknesses, and test how well an organization can detect and respond to threats.
Blue Team
The Blue Team is responsible for defending systems and networks. They monitor for intrusions, respond to attacks, and work on strengthening security measures to prevent breaches and recover from incidents.
Purple Team
The Purple Team acts as a bridge between the Red and Blue Teams. They encourage collaboration by sharing insights from both sides, helping organizations improve their security posture more effectively by enhancing both offensive and defensive strategies.
Top Hacking Platforms
Hack The Box is an online platform that offers a wide range of virtual machines and challenges designed to teach and test hacking skills in realistic environments.

TryHackMe provides guided cybersecurity learning through structured paths and hands-on labs, making it accessible for beginners and advanced users alike.

OverTheWire features a series of war games that teach foundational cybersecurity skills by progressively increasing in difficulty, helping users build their knowledge step-by-step.

Hack This Site is a long-standing, nonprofit hacking platform that offers free training missions designed to teach users about web security, coding, and realistic exploitation techniques in a hands-on way.

Top Services
Software & Hardware
We offer a streamlined purchasing experience for both software and hardware through our trusted partners, Ingram Micro and Xcel Source Corp. By leveraging these partnerships, we provide access to a wide range of high-quality products and the latest technology solutions.
Security Cameras
We will assist in configuring a security camera that is purchased through us. Hardware installation service is not available from us. We get our camera's from Reolink directly since we have a partnership with them.
Business Cards
We also design and print professional business cards for both new and existing businesses. Whether you're launching a startup or refreshing your brand, we’ll help you create custom cards that make a lasting impression.
Top brands we work with
Encrypt/Decrypt & Hash verification
When you download a file from the internet — whether it’s a program, document, or installer — there’s always a risk that the file could be incomplete, corrupted, or even tampered with by someone with bad intentions. That’s why professionals use a process to verify the file's authenticity and integrity before trusting it. This animation visually demonstrates that process in a way that's easy to follow. It begins with downloading a file, then immediately runs a command to check the file’s “digital fingerprint” — known as a checksum or hash. This fingerprint is unique to that exact file, and comparing it to the original lets us know if the file has been altered or is safe to use.
After the integrity is verified, the file is encrypted, which means it’s securely locked using a method only authorized users can reverse. This step is important in environments where privacy, data protection, or secure transfer is critical. The animation then shows the file being decrypted, or unlocked, followed by one final hash check to confirm that nothing changed during encryption and decryption. This last step proves that the original file and the decrypted file are still identical.
By looping this animated terminal, even non-technical users can see that security isn't just about flashy tools — it's about clear steps that protect information. This visual helps bridge the gap between what cybersecurity experts do behind the scenes and what regular users need to understand in order to stay safe online.
Latest CVE/Vulenabilities & RSS Feed

CVE stands for Common Vulnerabilities and Exposures. It’s a global system used to identify and catalog known security weaknesses in software, operating systems, and devices. Think of a CVE as a digital “warning label” that tells the world, “Hey, there’s a hole in this software, and it could be dangerous if not fixed.” When security researchers or tech companies discover a vulnerability, they report it and a CVE number is assigned. This helps everyone — from tech professionals to everyday users — stay informed and protected.
These vulnerabilities are important because they can be used by hackers to break into systems, steal data, or even take control of a computer or network. For example, a well-known vulnerability called PrintNightmare (CVE-2021-34527) affected many Windows computers and could have allowed attackers to run unauthorized commands. Once made public, the CVE entry alerted IT teams and individuals to update their systems immediately, helping prevent cyberattacks.
Taking action on CVEs is critical. When you receive a software update, it often contains fixes for these exact vulnerabilities. Delaying or ignoring updates means your system may still be exposed — like leaving your front door unlocked after a break-in alert. Hackers watch these CVE listings too, so once a weakness is made public, it becomes a race between patching the issue and being attacked.
By staying up to date with security patches and system updates, you’re helping protect your personal data, devices, and even others connected to your network. CVEs are not just for experts — they’re a public tool to help everyone stay safer in a connected world.

Other Sources
How to verify a website is legit?
It is critically important to check the URL you’re accessing online because it plays a central role in maintaining your digital security and privacy. Many cyberattacks, especially phishing, rely on deceiving users with fake or lookalike websites that mimic legitimate ones. A malicious URL might only differ from a trusted one by a single character, yet lead to a site designed to steal your credentials or install malware. For example, a phishing site might look exactly like Facebook but use a domain like
faceb00k-login.com
. If you don’t carefully examine the URL, you may unknowingly hand over sensitive data to attackers.
Verifying the authenticity of a domain is equally important. Reputable companies secure their official domain names (e.g.,
paypal.com
or
microsoft.com
), and any variation — such as a misspelled word, added dash, or different top-level domain like
.net
or
.info
— may indicate an imposter or unofficial source. Typosquatting, where attackers register misleading domain names, is a common tactic used to exploit user trust and familiarity. These tactics can be subtle but extremely effective at deceiving even tech-savvy individuals.
Another key reason to check the URL is to ensure you are using a secure connection. Legitimate websites use HTTPS, which encrypts the data you send and receive, protecting it from being intercepted or altered during transmission. While HTTPS alone doesn't guarantee a website is safe, its absence is a red flag. Non-HTTPS websites put your login credentials, financial details, and personal information at risk by transmitting data in plain text that can be easily stolen.
Beyond phishing, untrustworthy URLs can expose your device to malware. Malicious websites may deliver viruses, ransomware, spyware, or forced downloads simply by being visited. These "drive-by downloads" often exploit browser vulnerabilities and can result in significant damage — from stolen files to locked systems. Checking the legitimacy of a URL before clicking helps protect your device from being compromised.
Finally, verifying URLs also protects your personal identity and online reputation. Attackers can use fake survey links, impostor social media profiles, or rogue donation pages to collect personal data or manipulate your online presence. By confirming a URL’s validity, you defend against falling into such traps and help prevent attackers from gaining access to sensitive information.
In short, the URL is your first line of defense online. A quick glance at the address bar can help you avoid fraud, malware, data leaks, and identity theft. If something feels off about a URL, trust your instincts — and don’t click.
Try out VirusTotal
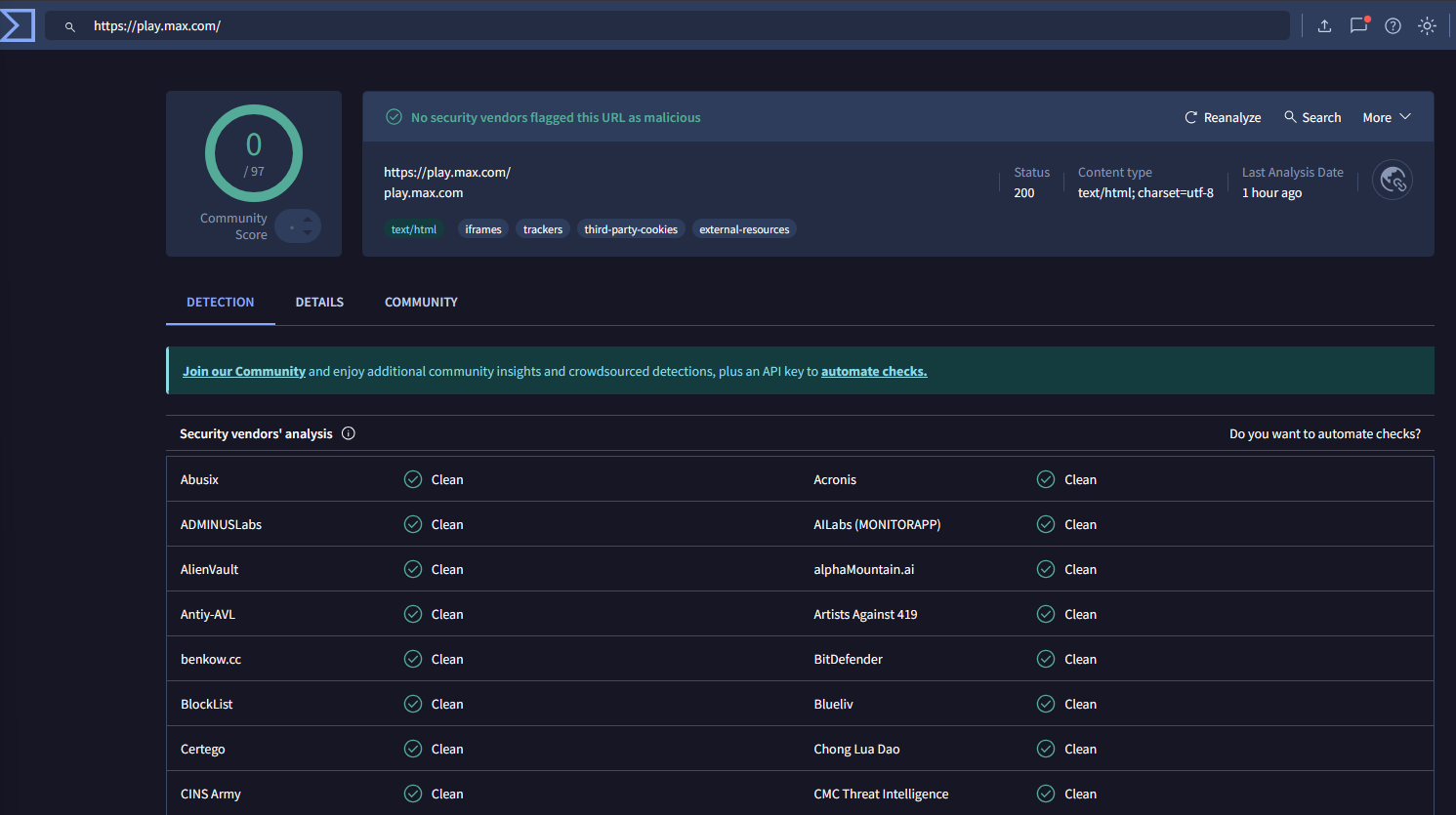
UNSAFE Website
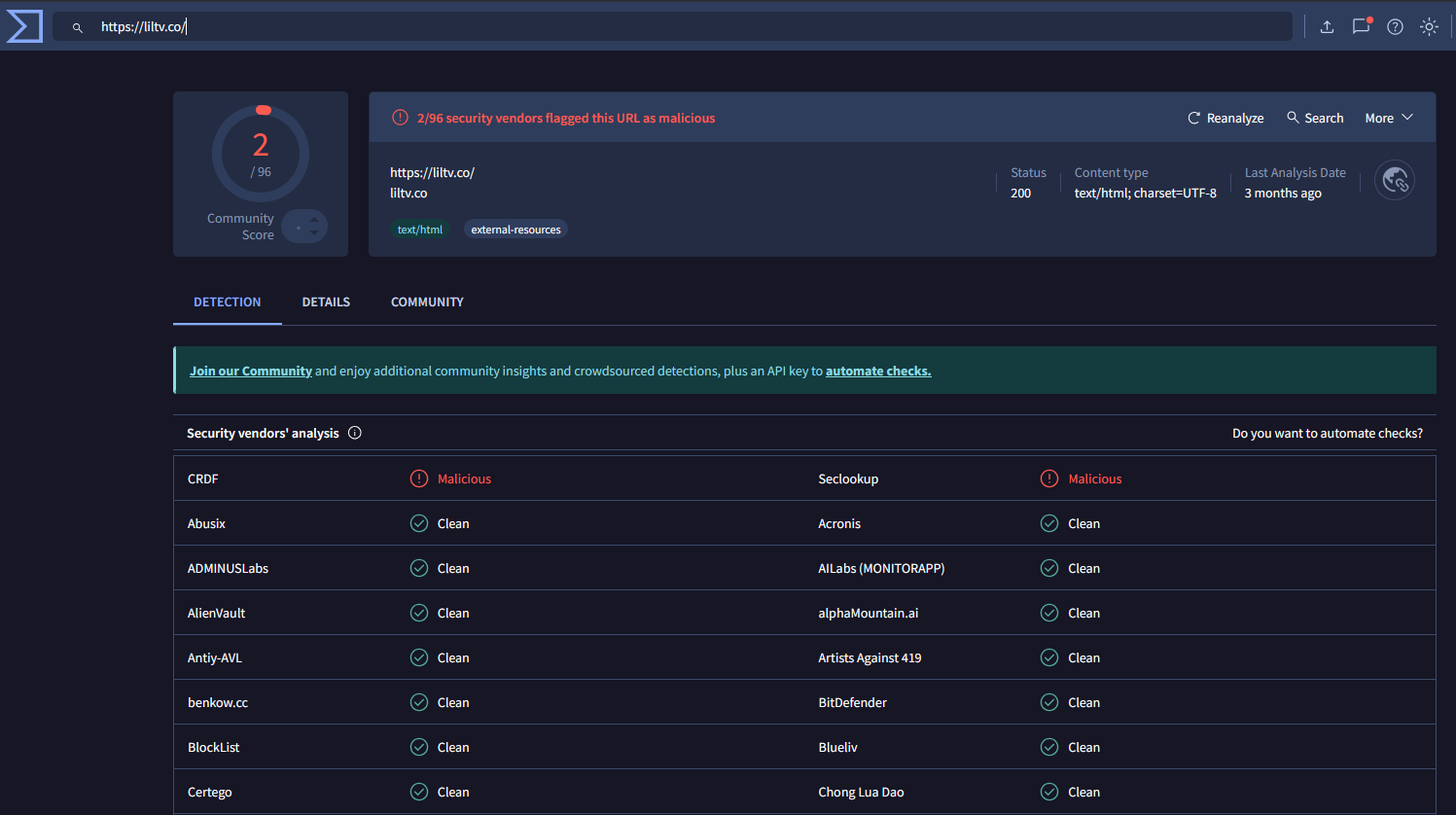
SAFE Website